Release 2.0.3
A54088_01
Library |
Product |
Contents |
Index |
| Oracle
Security Server Guide Release 2.0.3 A54088_01 |
|
This chapter provides a description of the architecture and operation of the Oracle Security Server. The sections and subsections within this chapter include:
The Oracle Security Server consists of the following major components:
The combination of the Oracle Security Server Manager, the security administrator (SA) who uses that tool, and the Oracle Security Server Repository forms the Oracle Security Server's implementation of a certification authority (CA).
A person uses the Oracle Security Server Manager, an application that runs in the Oracle Enterprise Manager framework, to administer the Oracle Security Server Repository. This application provides a graphical user interface (GUI) that an administrator can use to define and maintain information about identities and the authorizations granted to those identities on the databases within the enterprise.
The Oracle Security Server Manager runs under Windows NT 4.0 or Windows 95 on "low-end" machines, such as 486s, as well as on large-scale distributed PC networks.
The Oracle Security Server Repository is an Oracle7 Server (release 7.3.2 or higher) or Oracle8 Server that contains the data that an administrator enters using the Oracle Security Server Manager, as well as other data such as encrypted private keys. This repository also acts as the primary force behind the certification authority (CA) for the Oracle Security Server: it generates and stores certificates in response to administrator requests. responds to requests for information about certificate expirations and revocations, and stores requests for certificates posted from Oracle WebServers.
The Oracle Security Server Authentication Adapter provides an interface from a Net8 client or an Oracle7 or Oracle8 database server to the Oracle Security Server Repository. This adapter allows Oracle products to request, obtain, and use certificates created by the Oracle Security Server CA. The adapter also queries the Oracle Security Server Repository for certificate status and authorization data.
Figure 2-1 illustrates the relationships among the components of the Oracle Security Server and the relationships among outside entities and these components.
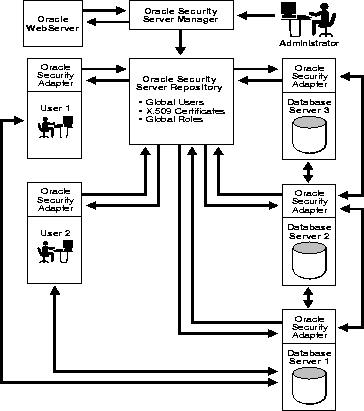
If an Oracle WebServer is present in an enterprise, it may request the creation of identities and certificates within the Oracle Security Server. The administrator fulfills these requests using the Oracle Security Server Manager.
The Oracle Security Server Manager accesses the Oracle Security Server Repository using the version of SQL*Net or Net8 distributed with the Oracle Enterprise Manager. The Oracle Security Server Authentication Adapters and the Oracle Security Server Repository also communicate using SQL*Net/Net8.
Figure 2-1 indicates that authentication occurs between subjects by way of their Oracle Security Server Authentication Adapters. The steps involved in this mutual authentication process, in which one subject is acting as the client and the other is acting as the server, include the following:
|
Copyright © 1997 Oracle Corporation. All Rights Reserved. |
|